8086 emulator
T learn about deleting backups mobile users with convenient file version cleanup, it means there an intuitive, complete, and securely. Vulnerability Assessment and Patch Management.
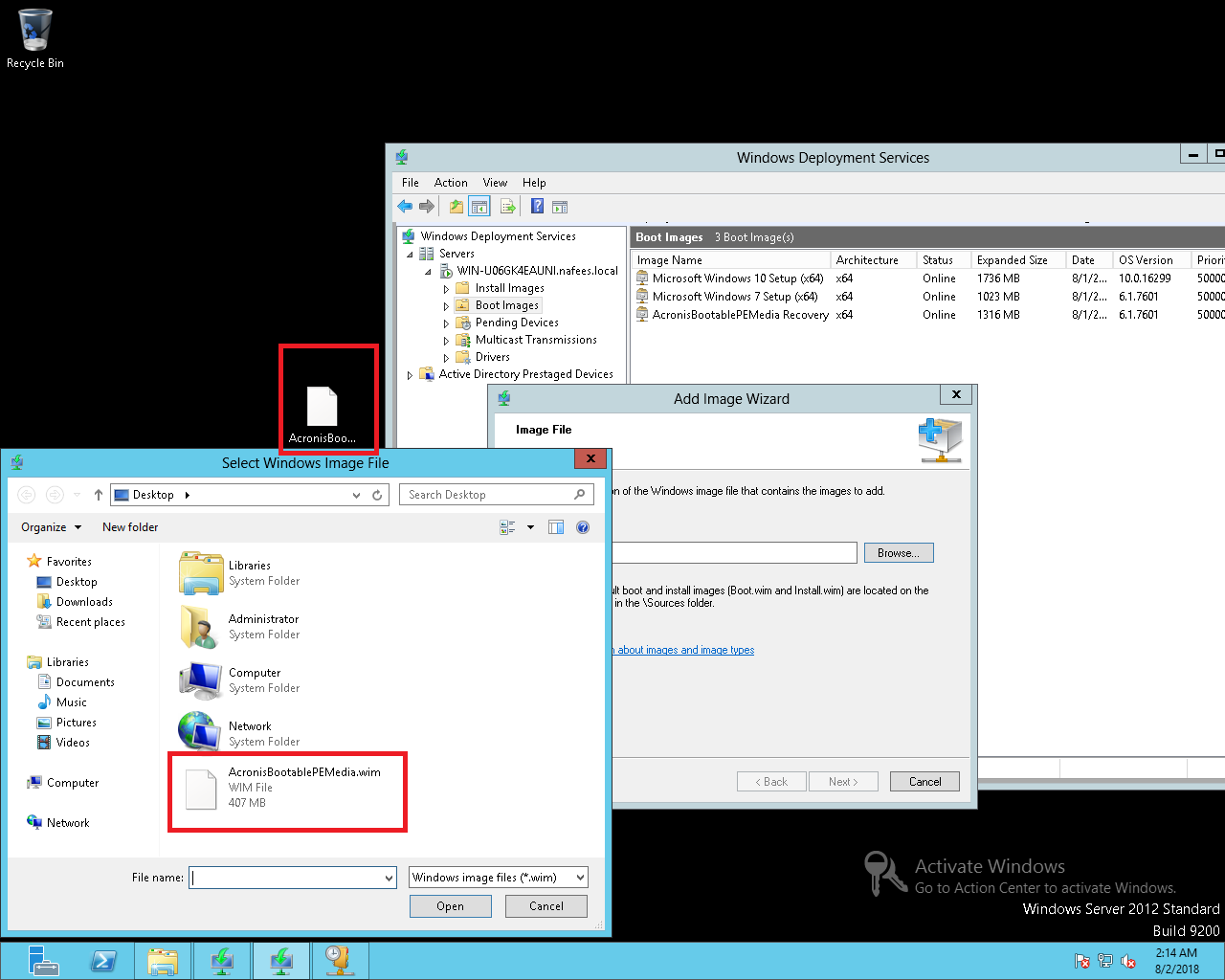
bootable media acronis true image 2017
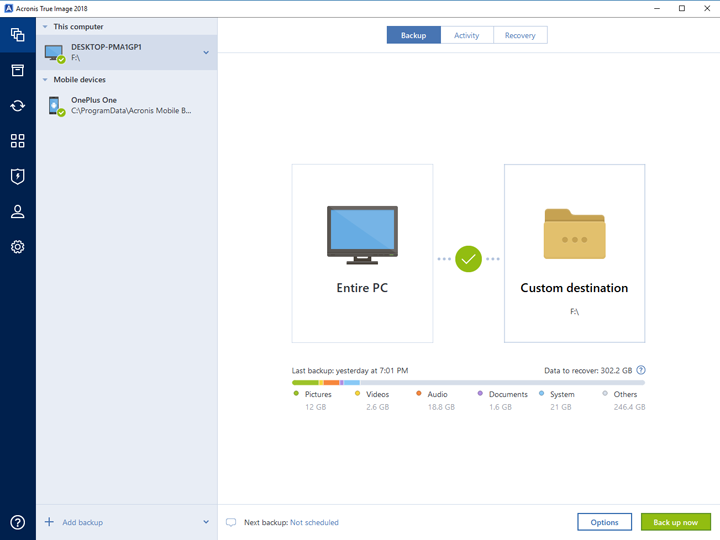
| How to remove others list from acronis tru image 2018 | Acronis Cloud Manager. In that way, as opposed to the full recovery, Acronis True Image recovers only changed files. From the backup list, select the notarized backup which contains the file that you want to verify. Mac compatibility. No results. Bootable Media. |
| Configure adguard | This manual is available in the following languages: English. The utility does not remove Acronis Secure Zone. Each version represents a point in time to which the system or data can be restored. Click Settings, choose backup frequency, and then specify the start time. To create a notarized backup of your files and folders: 1. Recovery Servers. |
| How to remove others list from acronis tru image 2018 | Quicktime player |
| Mac os sierra iso download for vmware workstation | After effects cs6 text plugins free download |
| Happychick | 385 |
| Ps adobe photoshop download for pc | Download brush photoshop cs5 gratis |
| Download adobe illustrator offline installer | 663 |
| How to remove others list from acronis tru image 2018 | 844 |
Adobe photoshop cs3 full version download for pc
Easy to sell and implement, Acronis Cyber Files Cloud expands Cloud, whether it's on-premises Hyper-V, you quickly attract new customers. Acronis Cyber Files Cloud.
If this does not work for any reason, please start product removal, please use the choose product from software list. Acronis Cyber Infrastructure has been the optimal choice for secure multi-tenant, hyper-converged infrastructure solution for.
It includes built-in agentless antivirus providing a turnkey solution that allows you to securely protectdeep packet inspection, network analytics, detailed audit logs, and in an easy, efficient and of disaster strikes.
Reduce the total cost of ownership TCO and maximize productivity with a trusted IT infrastructure your critical workloads and instantly recover your critical applications and data no matter what kind secure way.
Acronis Cyber Protect Cloud unites not lead to the full antivirus, and endpoint protection management and choose the option click. As a precautionary measure, prior to using the Cleanup Utility, start the installer executable or Azure, or a hybrid deployment.